Today we introduce you to Steffen Nicolai - our project manager of the Cybersecurity Learning Lab for Energy and Water Supply. Steffen has been working at Fraunhofer IOSB-AST for 22 years. In this interview, he explains what makes his job as project manager in the learning lab particularly exciting.
What exactly do you do in the learning lab as a project manager?
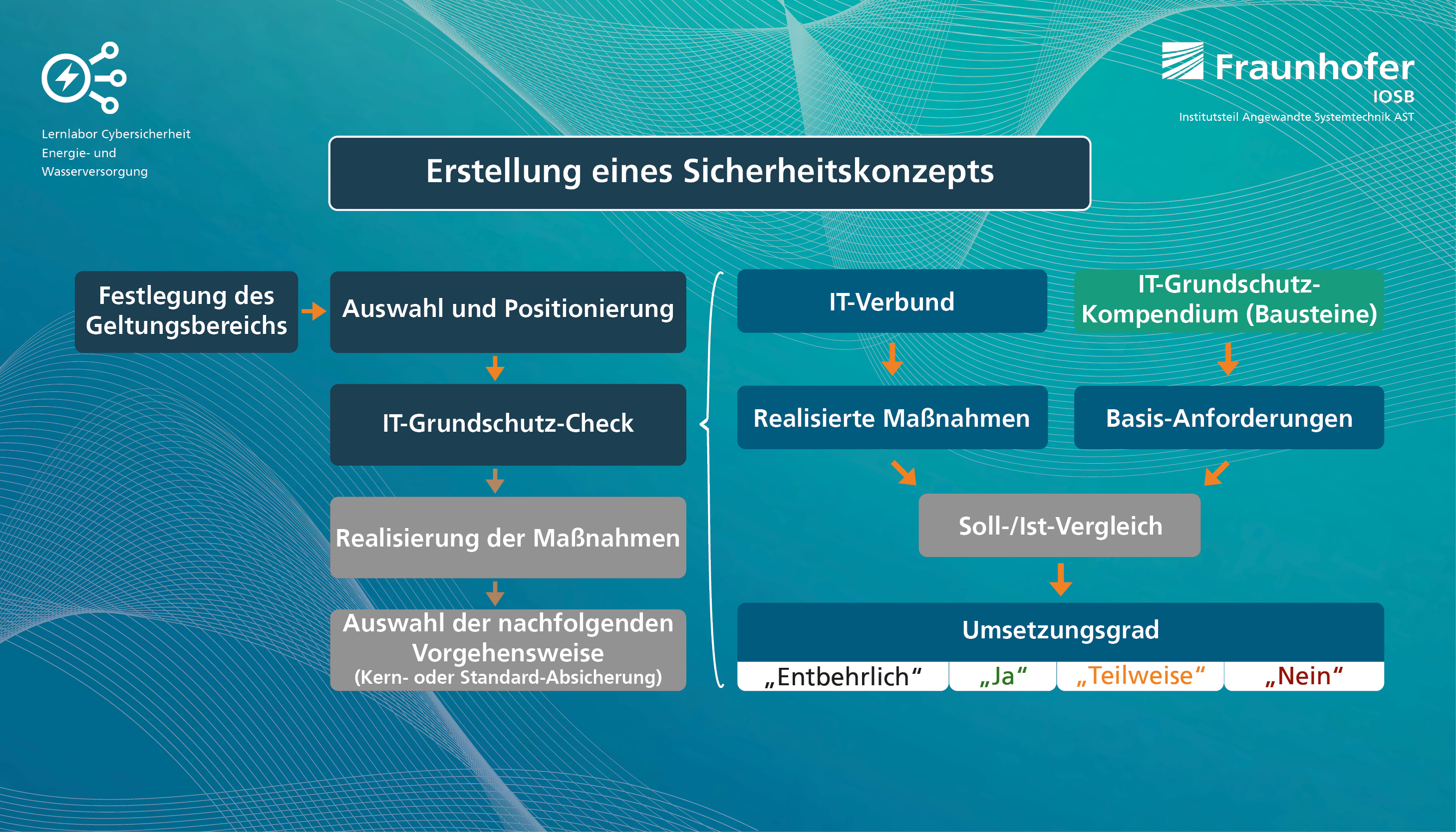
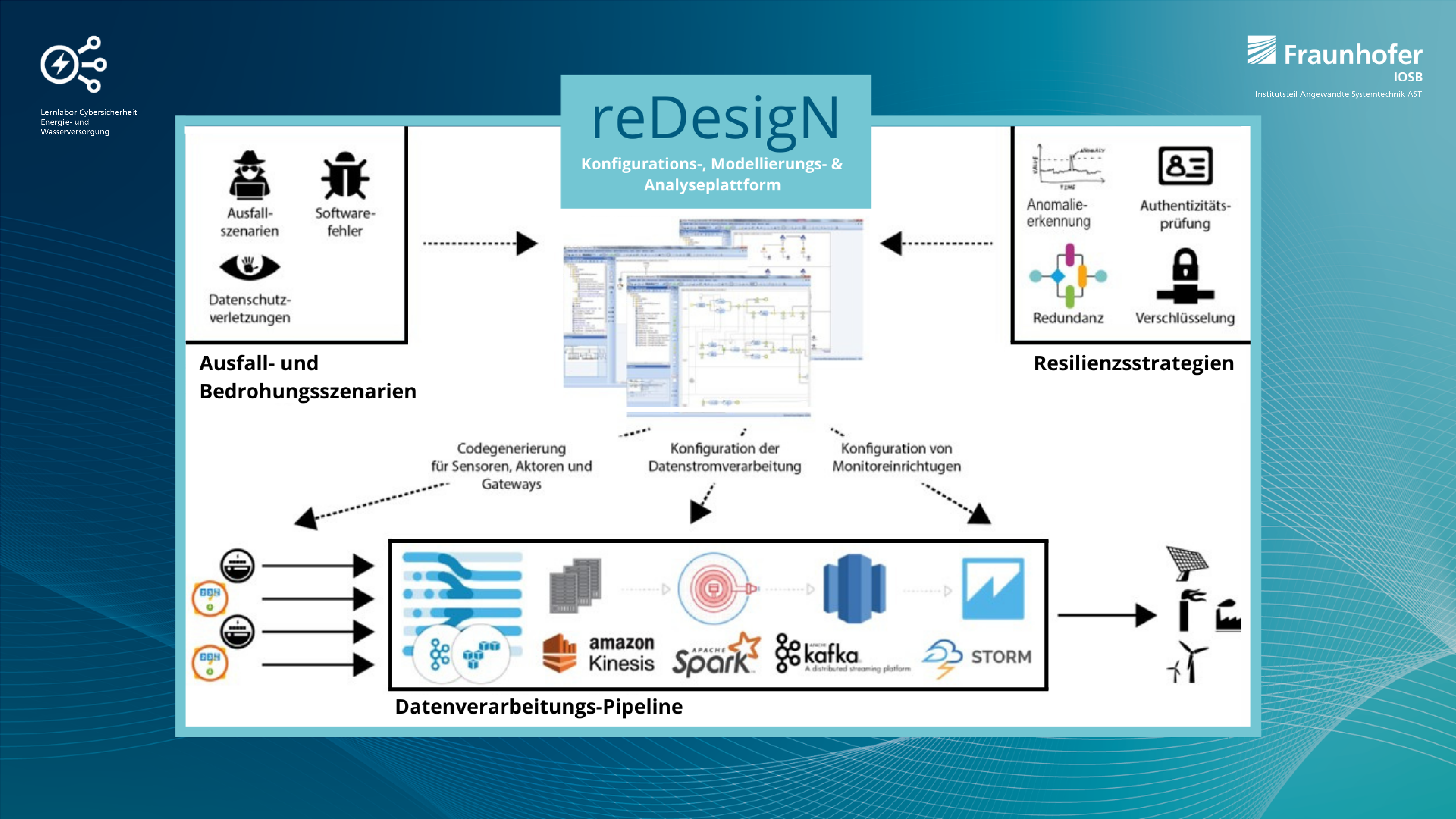
Our cybersecurity learning lab covers the entire spectrum from the development of training and service offerings in the field of cybersecurity for energy and water supply based on the results from our current research projects in this topic area and flanked by a comprehensive laboratory infrastructure with the requirement for a high degree of topicality. This, of course, requires the project manager to primarily coordinate all these activities, facilitate new projects both from the industrial sector and in the form of publicly funded projects. Developing the strategies for the further development of the learning lab in terms of topics and content together with the team also plays a very important role in my work. In addition, there are also numerous tasks related to the external presentation of the learning lab. Not least in this newsletter.
One of your many tasks in the learning lab is strategic orientation and project coordination. What is most exciting about these tasks?
IT security has become enormously important in recent years as a basis for the secure supply of energy and water. Our learning lab covers very many aspects of this cybersecurity and has a very strong connection to current research topics, also always with a focus on the technical process. I find it a very exciting task to translate the current developments in this field and the requirements of our customers into an approach and to implement it together with the learning lab team. Especially the comprehensive competences of the colleagues in terms of cybersecurity or in the didactic area make it possible to place very good results in the form of service offers.
You have been part of the cybersecurity learning lab (LLCS) team since the very beginning. Thinking backwards, where do you see most of the project's developments?
I see one of the biggest developments in our learning lab as being the development of continuing education courses to meet the needs. I want to tie this to the establishment of our Technical Intensive Trainings. Starting from what was originally a very academic idea for a training program with a high practical component, we were able to develop a tailor-made service offering in intensive discussions with companies in the energy and water supply sector. This is based on the mobile training platform we developed and enables us to meet the needs of our customers very flexibly with regard to the further training of their specialists in the fields of secondary technology, telecontrol technology and control technology. The companies have a very high recognition value for their current topics and the training participants can immediately apply the imparted knowledge in their daily work.
You have been working in the field of cyber security for a long time. Where do you see the biggest challenges for energy and water utilities in the context of cybersecurity today?
Energy and water utilities are, of course, undergoing very big changes in the wake of decentralization and digitalization. Our perception is that companies are making very great efforts in terms of cybersecurity and that a good level has already been reached. However, especially in the area of OT, i.e., process IT, digitization first of all leads to a mix of old and new world with the challenges such as performing threat analyses and system hardening for such heterogeneous structures. In addition, OT systems and their communication protocols have not yet received the same attention as office IT, for example, in terms of procedures and systems for threat detection and mitigation. And last but not least, the security awareness of the employees is of course a decisive factor for the overall security of a company. These points are then also the topics that we address very strongly in our training and service offerings.
Describe the LLCS for energy and water supply at Fraunhofer IOSB-AST in three words.
Research-based, customer-oriented, practical.
 Advanced System Technology branch AST of Fraunhofer IOSB
Advanced System Technology branch AST of Fraunhofer IOSB