February 2022 issue

Our services for you:

IT security for energy and water supply.
To adequately protect against ubiquitous threats, threat awareness and sensitization is very important. The human factor plays a significant role in IT security and the prevention of security incidents. We will give you an overview of current standards or regulations and work with you to assess how to implement them in your company. The awareness workshop sustainably promotes forward-looking and security-relevant behavior in your company.

Secure configuration and protection of the energy supply infrastructure.
In this training, the approach of hackers to energy supply systems and processes is explained structurally and reproduced through example attacks on the training platform. The entire cyber kill chain is run through and the multi-stage procedure during an attack is reenacted. Above all, preventive measures for network protection and system hardening are in the foreground. The focus is on practical relevance through the independent configuration of technical components and implementation of the developed security measures.

Be prepared! Evaluate and improve your own security standard
It's not a question of if, but when the next wave of attacks will hit you. That's why it's essential to conduct a comprehensive security assessment of your IT systems, networks and ICS assets to identify vulnerabilities and best protect yourself from potential threats. Stay one step ahead of attackers and identify potential risks before they can negatively impact your business security. Determine and assess your current threat situation with the help of our experts. Use detailed reports to determine the action required to ensure the continued availability and reliability of your operations.
Our cybersecurity courses are based on years of innovative and intensive preliminary research. We are always developing new methods and procedures to detect and defend against cyber attacks.
Now you can benefit from our expert knowledge! Make 2022 the year you lead the way with cybersecurity and secure your organization against attacks.
Do you have an acute concern, security concerns or would you like to have your systems put through their paces? Then feel free to contact us, together we can discuss measures on how we can best support your business.
Are you interested in conducting a training course in your company for your employees?
Then please contact us and together we can develop a seminar program, tailor-made for your company and its needs.
If you have any questions, we are always available and happy to advise you.
Now you can also always reach us by e-mail at: schulung@iosb-ast.fraunhofer.de.
Have we aroused your interest? Then take your chance now and register for one of our cybersecurity courses:
Research: Innovative testbed for testing a new generation of IT/OT security systems
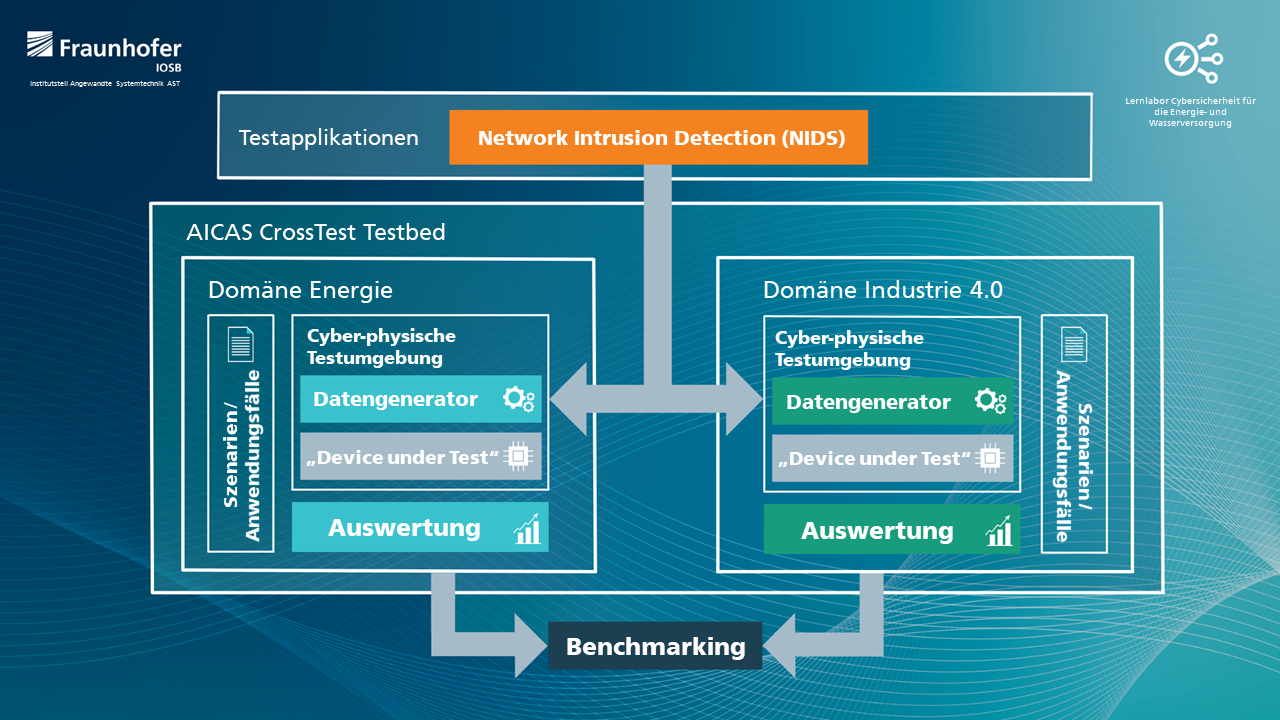
The AICAS project, which runs from November 2019 to September 2021 and is funded by the BMBF, addresses the topic of AI-assisted detection of security incidents. Under the funding guideline "German-Israeli Cooperation in the Research Fields of Civil Security and IT Security", two leading industrial partners in this field, Rhebo GmbH from Leipzig and Radiflow Ltd from Tel Aviv, were involved in addition to Fraunhofer IOSB and Fraunhofer IOSB-AST. The aim of the project was to test the use of AI for intrusion detection systems (IDS) and to evaluate it on the basis of various use cases and scenarios in the domains of "industrial production" and "energy supply".
In the research project, different machine learning methods were investigated and evaluated for their applicability to anomaly detection in industrial environments. These included anomaly and attack detection based on network traffic, as well as on recordings from monitoring solutions and other sources of information such as log files. The primary goal within the project, besides the detection of attacks or anomalies, was the classification and assignment to known attack methods. For this purpose, two testbeds were designed and implemented within the project which could provide exemplary, realistic data sets for the development and testing of AI methods for the two domains "industrial production" and "energy supply". For data generation, known attack patterns and techniques were defined as scenarios and implemented within the testbeds. Based on these datasets of various IT attacks, the commercial systems of the industry partners could be tested in the lab environment and their behavior could be included for downstream AI approaches for classification. As a result of the AICAS project, the generated datasets will be published and can be used as benchmark datasets for e.g. system vendors. Furthermore, with the data generator realized in the project, it is possible to create data sets specifically adapted to the requirements of industrial customers from the aforementioned domains for the most diverse attack scenarios and techniques.
Introducing the staff* of the Cybersecurity Learning Lab for Energy and Water Utilities:

In this section we would like to introduce you to our colleagues. Today we introduce you to Dennis Rösch - our research assistant. Dennis has been working in the cybersecurity learning lab for energy and water supply for almost 5 years. He explains what makes his job as a research assistant in the learning lab particularly exciting in this interview.
What exactly do you do in the learning lab as a research associate?
Within the cybersecurity learning lab, I work both on accompanying research projects, whose findings are to be transferred to the various training formats, and on training delivery. The main challenge and at the same time the unique selling point of the learning lab is the transfer of research knowledge into practice-relevant training content. A training participant should learn about the current state of research with us, but also take away something directly applicable for himself. To achieve this, we combine current research with further training, and this transfer is one of my tasks in the learning lab.
One of your many tasks in the learning lab is to conduct training courses for companies in the energy and water supply sector. What qualities should a speaker possess?
From my point of view, a speaker should first and foremost have technical expertise and be able to communicate this well. In my opinion, it is particularly important to build a bridge to the everyday challenges of the training participants and to motivate the participants to master these challenges with what they have learned.
You have been on the team of the Learning Laboratory Cybersecurity (LLCS) for several years now. How do you like it so far and how have you been able to develop?
For me, getting involved in the topics of the Cybersecurity Learning Lab also meant a new thematic orientation. From university education, I come from automation and systems engineering, which unfortunately is not yet fully related to cybersecurity in education. I think it is very exciting to look at automation processes directly from a security perspective. The application of systems engineering methods also plays an important role in various areas of IT security. Thus, I can transfer my existing knowledge to an exciting subject area and learn and develop daily on new and specific cybersecurity challenges.
What are you really good at?
I think I am very good at approaching complex problems in a structured, analytical and goal-oriented way. In my daily work, I often encounter new challenges to which we try to find answers as a team. There, structured approaches are very important for me.
Describe LLCS at Fraunhofer IOSB-AST in three words.
Versatile, challenging, demand-oriented
Our training offers:

You can find the current training dates here:
 Advanced System Technology branch AST of Fraunhofer IOSB
Advanced System Technology branch AST of Fraunhofer IOSB