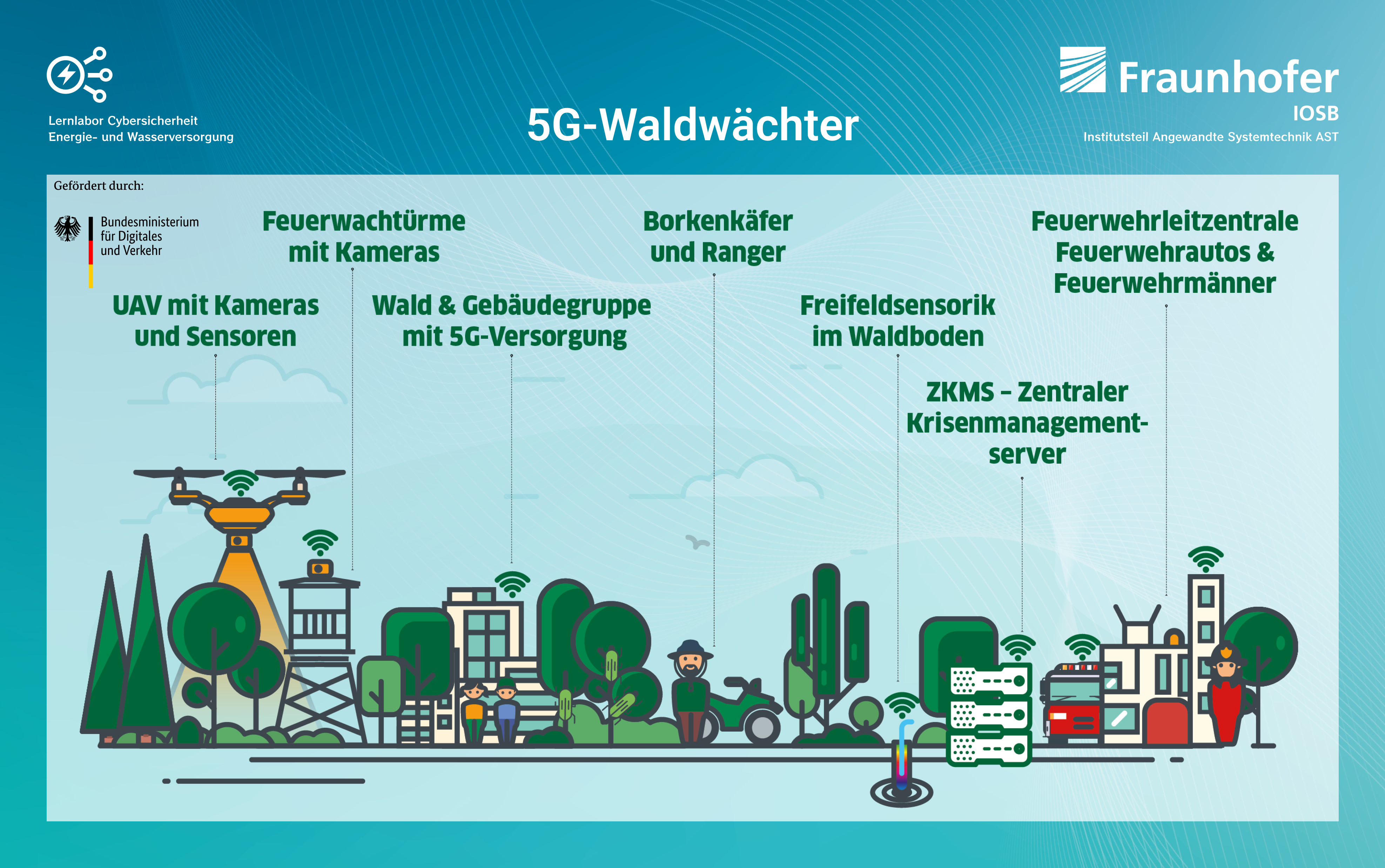
Forest health is threatened by many factors. In addition to global warming, forest fires and pest infestations are among the greatest threats. As part of the 5G Forest Guard project, a new technological and methodological approach is being tested that will make it possible to detect both forest fires and pest infestations in the formation phase. This should enable fire departments and forest owners to take appropriate countermeasures at an early stage and thus minimize potential damage to the forest. The concept includes two complementary applications for forest fire source identification and bark beetle detection.
To identify a potential forest fire source, the project area will be monitored using stationary and mobile camera technology in different spectral ranges. In addition to existing fire watch towers, UAVs will be equipped with appropriate technology. Image and thermal data will be collected at regular intervals and stored on a server. As soon as the data is received there, it is automatically examined on the server using AI algorithms with regard to any deviations from the "normal state". The project area is further equipped with sensor technology. The deviations detected can thus be compared with the data from the sensors. At the same time, a UAV goes to the location of the potential fire source and continuously collects up-to-date data. If the AI detects a potential source of fire in the deviation, corresponding information is issued to the fire department for a decision on further measures. The subsequent firefighting operation can then be monitored using the technology on the UAVs.
The same technology and data infrastructure are used to detect bark beetle infestations. However, image data from multiple spectral regions are processed here. Using the red edge method, a deviation of the chlorophyll content in the trees can be detected. Special sensor technology that detects odors indicating bark beetle infestation can support this system. In the end, the forest owner receives information on the potential infestation. This methodology can indicate an infestation earlier and in a more targeted manner than the visual examination by forestry staff during a forest inspection, which is common today.
Both applications are characterized by their ability to detect the threat earlier than conventional methods. This enables the timely effect of appropriate control approaches and the minimization of damage to the forest. The overall concept includes the use of already existing infrastructures (e.g. fire watchtowers), which are optimized in terms of their technical equipment for the project purposes. The success of the project depends on stable high bit-rate data transmission. The 5G Forest Guard project therefore relies consistently and without alternative on 5G.
The 5G standard is designed for industrial and business use cases. Advantages such as the high data rate, very low latency or low energy consumption (relative to the amount of data) are always emphasized. In the project, the measurement data from a large number of sensors are the basis for data evaluation and are therefore essential for decision-making to take action (e.g. sending out the fire department in the event of a detected forest fire). Fundamentally, therefore, sensors significantly influence the decisions made and the behavior of personnel based on them, as well as the control and coordination of resulting actions. Availability, integrity and confidentiality of sensor data are therefore the protection goals to be achieved in the context of information security.
The focus of Fraunhofer IOSB-AST in the project work is on the security aspects. On the one hand, this means the secure integration of the sensors and sensor data. It is examined which measures are necessary and feasible within the framework of the requirements in order to counteract misuse of these. On the other hand, securing the data communication between the drone and the base station is necessary. In the application context, for example, direct access to the drone is envisaged (image data, position) as well as the connection of terminal stations to a central evaluation server for the purpose of data updates. High security standards must also be met for real-time control of the drone over long distances. It is therefore being evaluated which security features are already included in the 5G standard and for which use cases they are suitable. In addition, established IT security measures will be analyzed and integrated into the system, especially with regard to available resources and performance parameters.
Funding is provided as part of the 5G Innovation Competition of the Federal Ministry of Digital Affairs and Transport (BMDV). The 5G Forest Guard project builds on the cooperation of various partners with different core competencies and is composed of administration, companies and research institutions in an interdisciplinary manner. These include the district of Görlitz as consortium leader, Fraunhofer IOSB-AST, Zittau/Görlitz University of Applied Sciences, Brandenburg University of Technology Cottbus - Senftenberg (BTU) and GGS - Geotechnik, Geoinformatik & Service GmbH. In addition to these project partners, two mobile communications companies, Telekom and Vodafone, have been acquired as associated partners. Furthermore, the military training area Oberlausitz supports the project, among other things by providing the project area.
 Advanced System Technology branch AST of Fraunhofer IOSB
Advanced System Technology branch AST of Fraunhofer IOSB