Service offering: Guidance on the use of attack detection systems
With the enactment of the 2nd IT Security Act, operators of critical infrastructures are obliged to take appropriate organizational and technical precautions to prevent disruptions to the protection goals of "availability", "integrity", "authenticity" and "confidentiality". In order to implement this across the board, the new Section 8a (1a) of the Federal Office for Information Security Act (BSI Act - BSIG) explicitly refers to the introduction of systems for attack detection (SzA) [1]:
"Attack detection systems in the sense of this law are processes supported by technical tools and organizational integration for detecting attacks on information technology systems. In this context, attack detection is performed by comparing the data processed in an information technology system with information and technical patterns that indicate attacks."
(Section 2 (9b) BSIG)
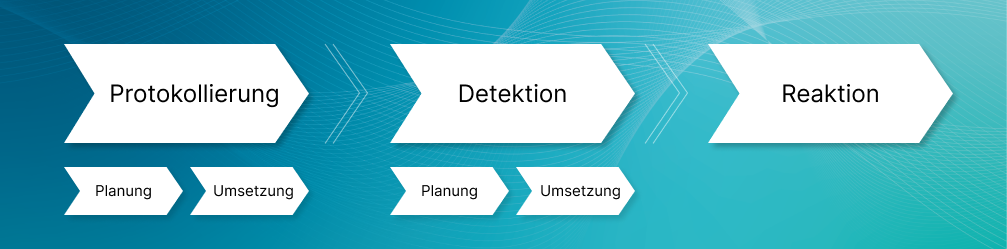
For the implementation, the BSI published an orientation guide for the use of attack detection systems on 29.09.2022 [2], which describes the introduction of SzA for operators of critical infrastructure by defining three task areas: Logging, Detection, and Response (see figure).
The various steps of planning and implementation require above all the fundamental analysis of one's own infrastructure as a basis on the way to successful planning and implementation of suitable systems.
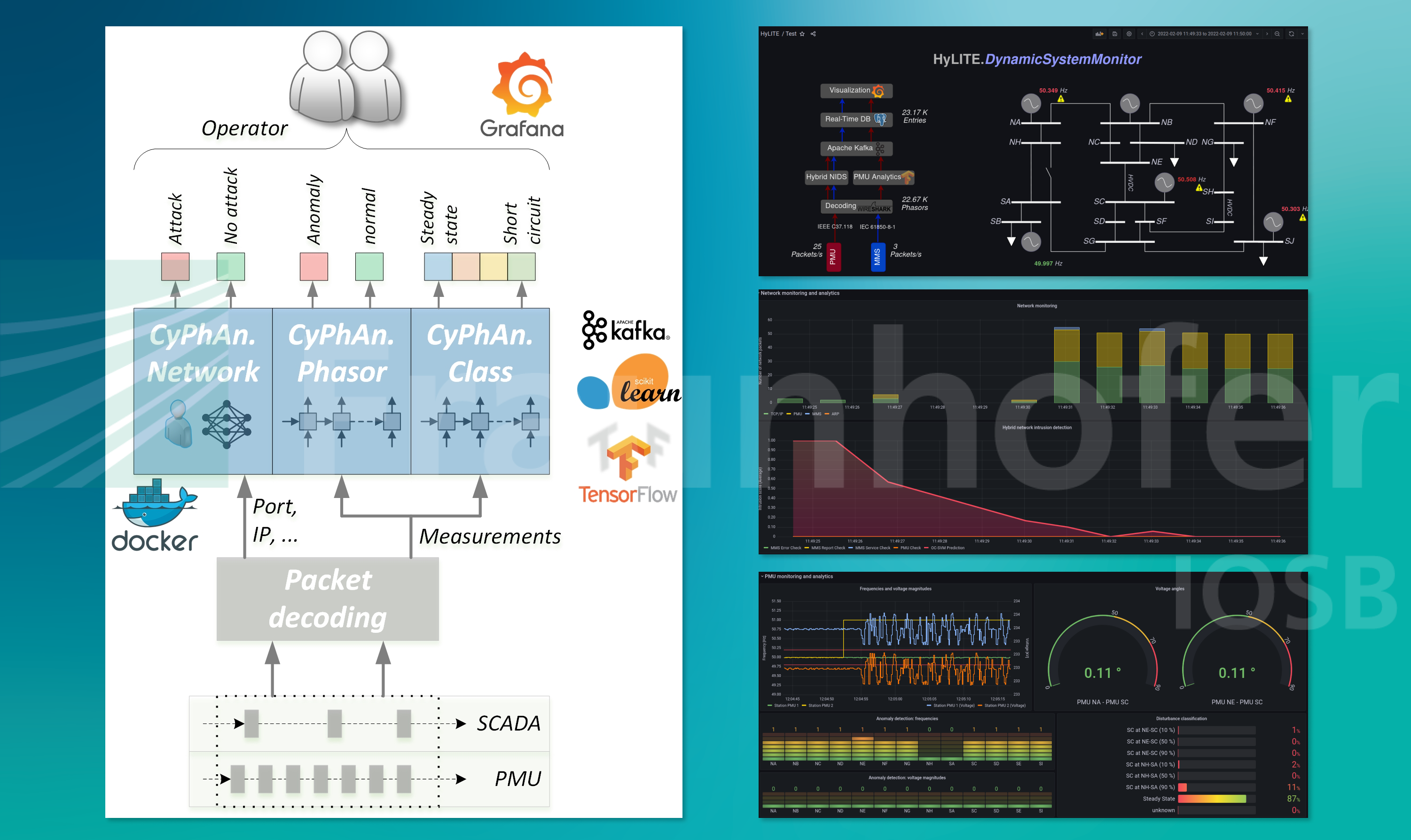
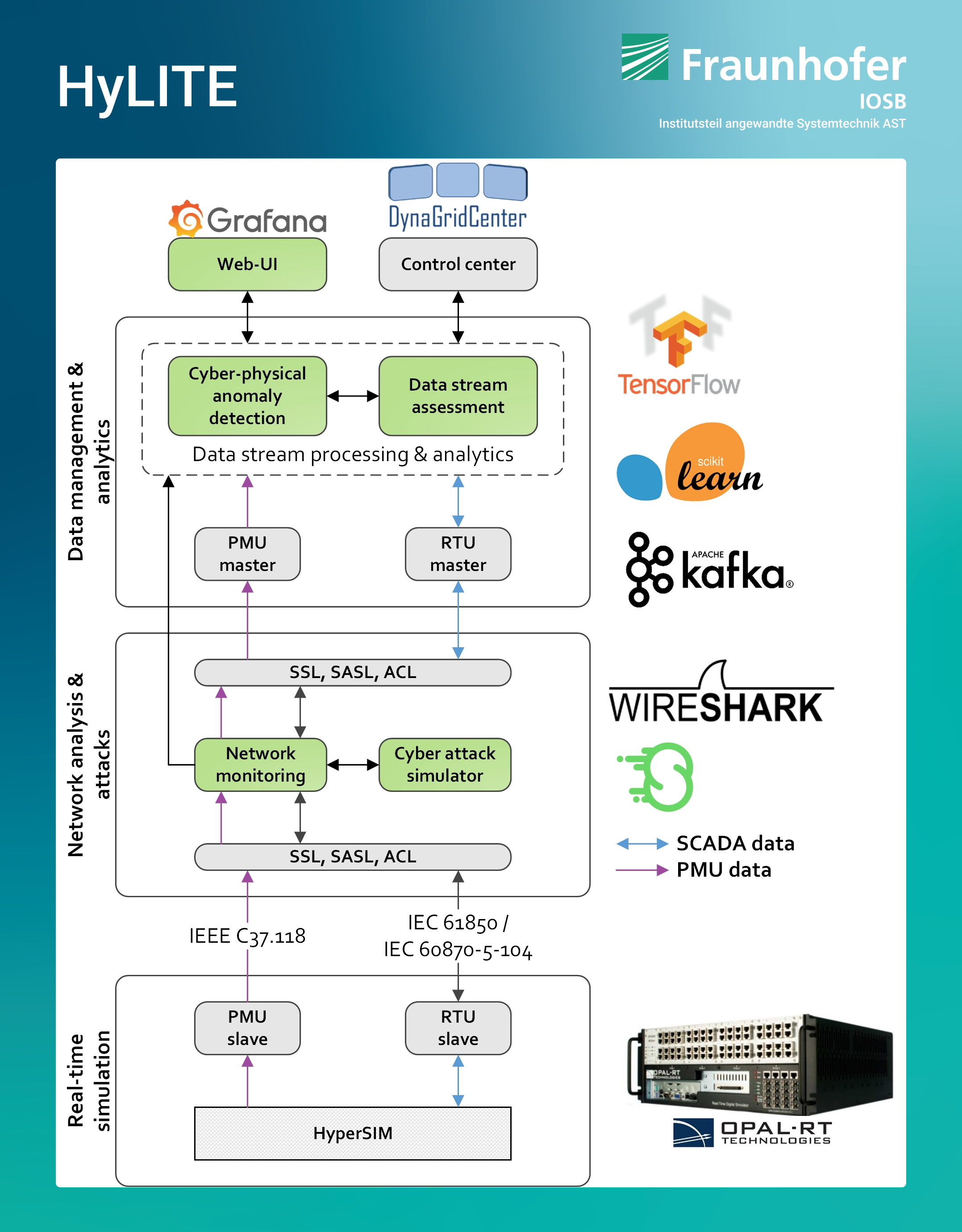
We will be happy to support you on the path to compliance with Section 8a (1) and work with you to develop concepts for the successful introduction of the SzA in the specific circumstances of your company and your process structures. We will address this topic more explicitly in the next issue.
[1] https://www.gesetze-im-internet.de/bsig_2009/__8a.html
[2] https://www.bsi.bund.de/SharedDocs/Downloads/DE/BSI/KRITIS/oh-sza.pdf
 Advanced System Technology branch AST of Fraunhofer IOSB
Advanced System Technology branch AST of Fraunhofer IOSB